With the advent of quantum computing, organizations must transition from legacy authentication methods to post-quantum authentication (PQA) before Q-Day — the point when quantum computers can break conventional encryption. However, switching to PQA isn’t just a technical upgrade; it’s a transformation that impacts user experience, security, and compliance.
One of the biggest challenges is migrating users securely while maintaining trust. This article outlines three key migration strategies for organizations making the transition. Each comes with its advantages and drawbacks.
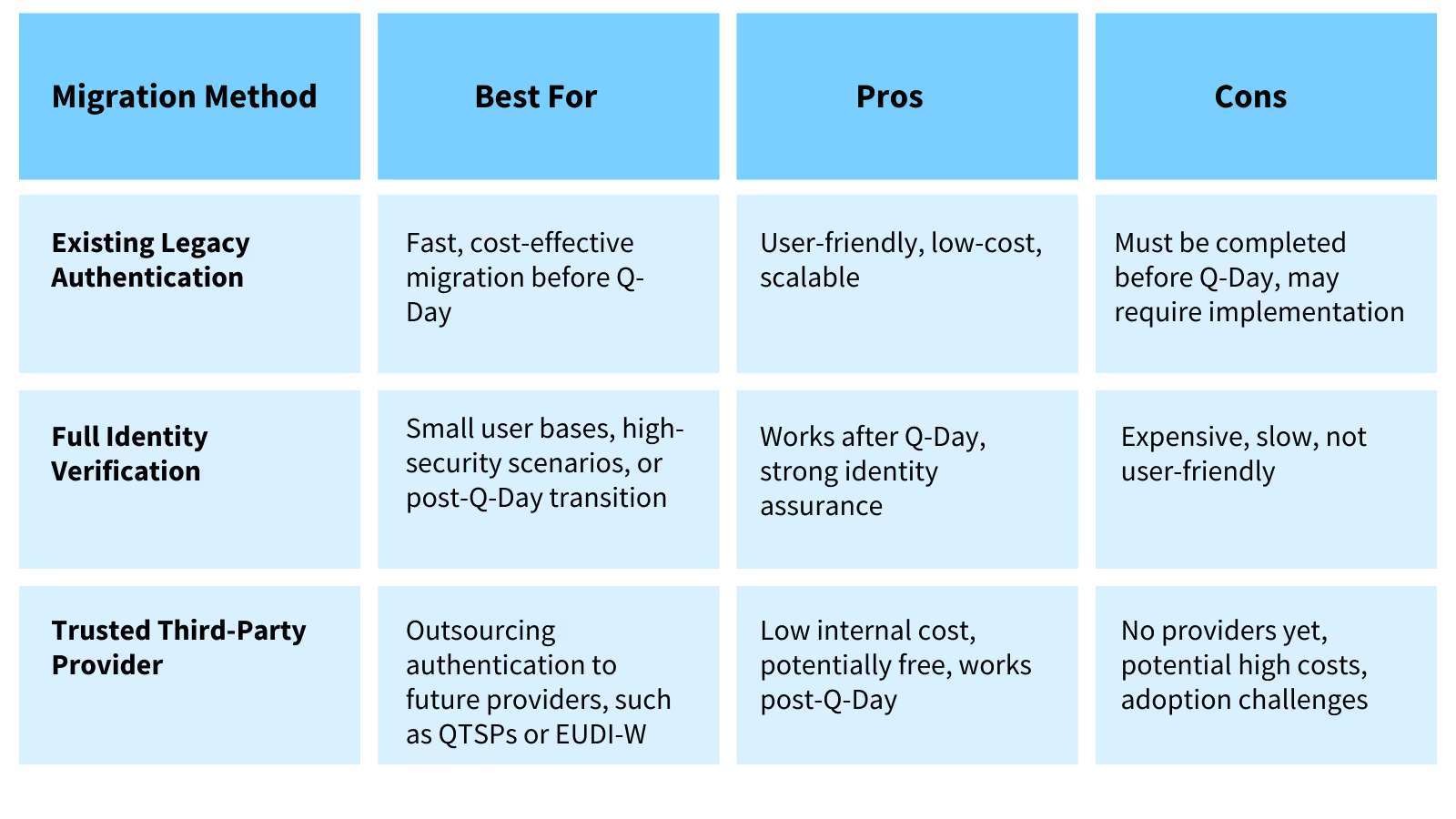
1. Enrollment via Existing Legacy Authentication
How it works:
Organizations leverage their current authentication methods (e.g. passwords, PINs, or legacy cryptographic keys) as proof of identity for enrolling users in post-quantum authentication. This method must be executed before Q-Day, as legacy authentication will no longer be secure afterward.
Pros:
- User-friendly: Users simply authenticate using their existing credentials, making the process seamless.
- Cost-effective: Minimal additional infrastructure investment is required, making it scalable for large user bases.
Cons:
- Time-sensitive: This method becomes untrustworthy post-Q-Day, forcing organizations to complete migration well in advance.
- Implementation effort may be required: Some organizations may need to develop new processes if they lack a built-in mechanism for transitioning authentication elements.
Best for: Large organizations with a broad user base looking for a low-cost, fast migration strategy before Q-Day.
2. Enrollment via Full Identity Verification
How it works:
Users undergo full identity verification — either in person or online — before being enrolled in post-quantum authentication. This can include identity document verification and advanced biometrics (e.g. facial recognition with liveness checks).
Pros:
- Not time-sensitive: This method remains valid before and after Q-Day.
- Works for new customers as well: Unlike the legacy authentication method, this approach can also be used for customers who are enrolling for the first time.
- Stronger identity assurance: Provides a higher level of security, reducing fraud risks.
Cons:
- Expensive: Identity verification is costly, particularly when scaling to a large user base.
- Cumbersome for users: Requiring users to undergo verification may create friction and lower conversion rates.
- Slower process: Compared to using existing authentication, verifying each user individually takes longer.
Best for: Organizations with a small number of users, high-security needs, or those transitioning users after Q-Day.
3. Enrollment via Trusted, Quantum-Resistant Third-Party Provider
How it works:
Instead of performing identity verification internally, organizations can outsource user authentication to a third-party provider offering quantum-resistant authentication (e.g. a government digital identity program or a Qualified Trust Service Provider [QTSP]).
Pros:
- Not time-sensitive: This method can be used before or after Q-Day.
- Lower internal implementation cost: Offloads authentication and identity verification responsibilities to a trusted provider.
- Potentially free: If supported by government initiatives like the EU Digital Identity Wallet (EUDI-W), costs may be subsidized or free.
Cons:
- No suitable providers yet: At present, no established QTSP or government service offers post-quantum authentication — though this may change.
- User adoption challenge: Requires users to enroll in an external system, which could be an adoption barrier.
- Cost unpredictability: Commercial providers may charge high fees.
Best for: Organizations looking for a future-proof solution that outsources authentication to trusted providers once quantum-safe identity services emerge.
Choosing the Right Migration Path
Each migration strategy balances security, cost, and user experience differently.
For organizations with large customer bases, legacy authentication enrollment offers the best balance of cost and efficiency, but it must be completed before Q-Day. If organizations miss the pre-Q-Day window, they must fall back on full identity verification or third-party providers — which may be costly or not widely available.
Whichever path you choose, the time to act is now. Organizations should begin planning their migration strategies by 2026 to ensure they meet post-quantum security requirements before the quantum threat becomes a reality.
Ready to Future-Proof Your Authentication?
At Wultra, we are leading the charge in post-quantum authentication with our mobile-first authentication solution built for banks and fintechs. Our latest version supports hybrid cryptography, combining traditional elliptic-curve cryptography (ECC) with post-quantum algorithms like ML-KEM and ML-DSA.
Contact us at sales@wultra.com to discuss how we can help you migrate to quantum-safe authentication — before it’s too late.


.webp)